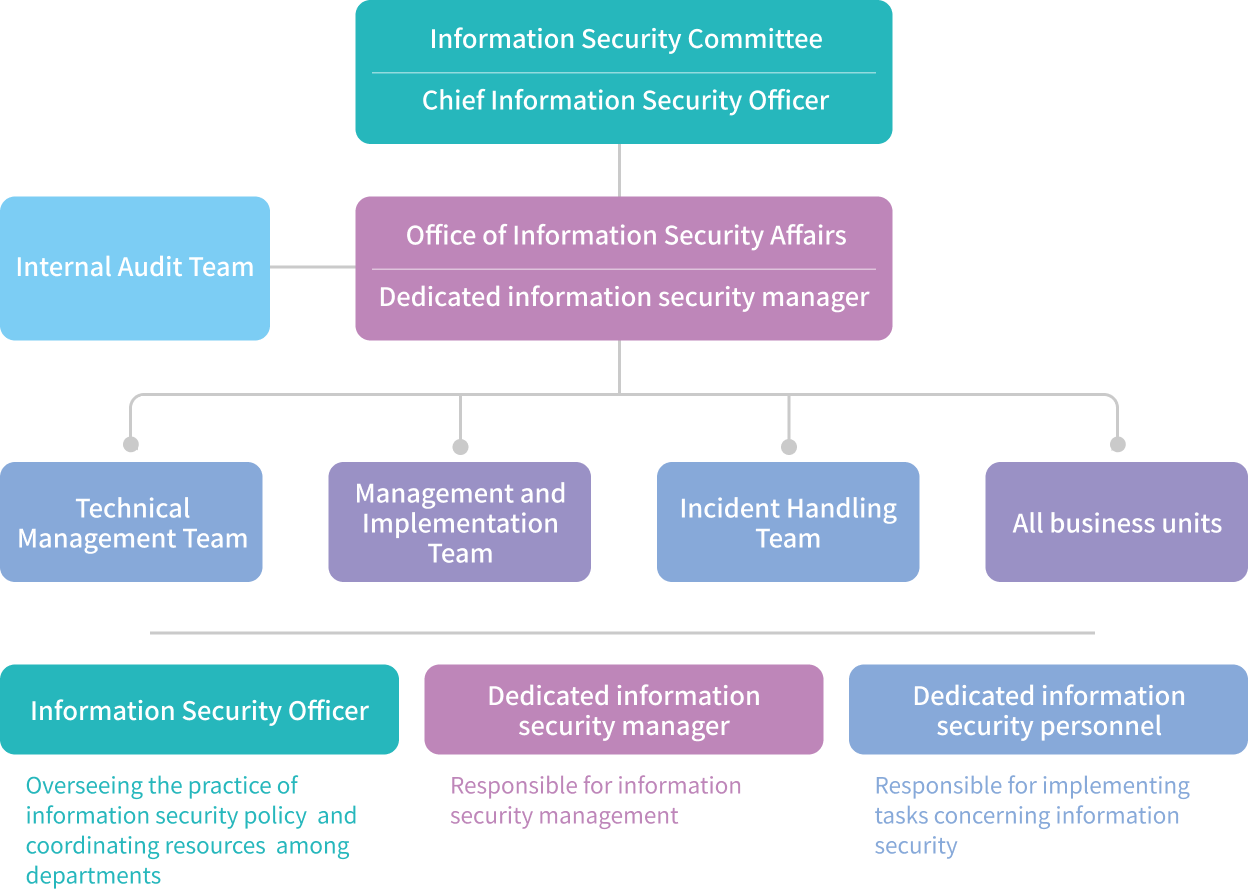
Information security governance system
In order to mitigate information security threats and risks arising from the application of emerging information technologies and environmental changes, Yulon Motor ongoingly optimizes its information security system, enhances defensive ability and adopts relevant internal operational regulations as required for a computerized information processing system in Article 9 of the“ Regulations Governing Establishment of Internal Control Systems by Public Companies” to make sure that all information-related operational procedures comply with standard procedures for information security. Since 2017, Yulon Motor has constructed the information security risk internal control measures, aligned with international information security trend and strengthened risk management for confidentiality in accordance with the Group’s information security development blueprint, which indicates the short-term principle for handling emergent threats, the mid-term principle for optimizing information security procedures and the long-term development with dynamic reviews and responses. Echoing to the variety of information security threats and the tremendous number of attacks in the industry, we joined the TWCERT/CSIRT alliance in the first half of 2022 to share information on defense.
Structure of information security management organization
The manufacturing service department is the responsible unit for the information security of Yulon Motor. Four IT officers and several professional personnel have been appointed to develop information security policies, devise and carry out information security operations, and promote information security measures. The unit also reports the general information security governance status to the board of Yulon Motor and the Yulon Group Administration Office on a regular basis. Moreover, in 2022, we established the Information Security Committee as required for all first-tier listed companies by the competent authority. The Information Security Committee is an internal task force of the Company, which holds one meeting for context analysis and one meeting for management review every year in accordance with ISO 27001.
Information security project organization
Information security management strategy
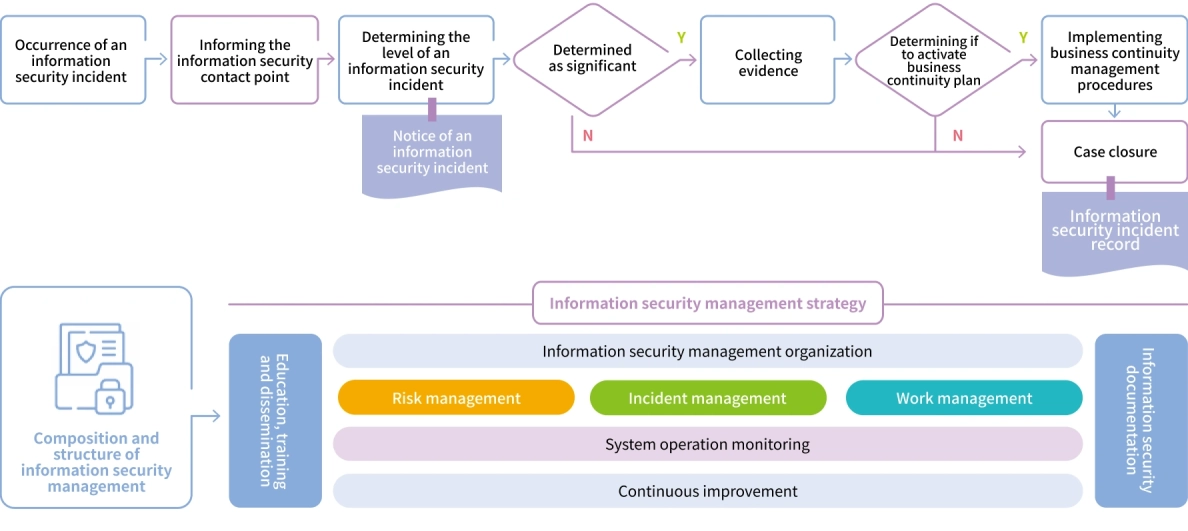
The PDCA cycle is adopted for managing Yulon Motor’s information security and ensuring the achievement of targeted reliability and constant improvement.
In order to manage information security risks, we respond to and prevent the occurrence of risk events from three aspects:
-
1Before the occurrence :Periodic independent inventory and inspection from the process and technical aspects, in order to proactively prevent information security incidents.
-
2When the event occurs: Damage control emergency response.
-
3After the occurrence: Tracking and inclusion in the prevention scheme.
Incident Response Process Flowchart for Cybersecurity Events
Performance in information security management and future plan
To reinforce the overall information security, a number of projects have been carried out in 2019–2022, including“ anti-hacker of internal and external network transmission,”“ employee information security awareness enhancement,”“ malicious website prevention and control,”“ remote work connection protection,”“ system vulnerability improvement/penetration test,”“ data leakage protection,” “cross-company off-site server room/backup enhancement,”“ IT management framework (ISO/ISMS) enhancement,”“ portable storage device control,”“ email system optimization,” and“ trade secret file management.” In 2022, there was not any complaint regarding infringement of customer privacy or loss of customer information. Looking ahead, we have laid out the blueprint for facilitating the“ Information Security Risk Internal Control Management Measures” to steadily roll out the overall medium- to long-term information security strategies that cover information infrastructure construction, smart manufacturing protection, and information security training. Based on the existing structure of information security internal control and with“ boosting the information security resilience” as the focus, we will strengthen the capabilities of“ effective screening and loss minimization, and rapid disaster reduction and recovery” to enhance the response capabilities to information security crises and business continuity management.




